Benefits
Monitor Network-Connected Devices
Monitors all devices connected to the network infrastructure. The Password Protection feature enables administrators to block unauthorized device access.
Comprehensive Email Security Scanning
Provides real-time scanning of all emails for viruses, worms, trojans, spyware, adware, and hidden malicious content using advanced heuristic-driven dual anti-virus engines.
Reduces IT Costs
Reduces security management costs through File Reputation Services, Asset Management, print monitoring, Active Directory integration, and comprehensive support for VMware, SYSLOG, SNMP, Network Access Control (NAC), and Network Access Protection (NAP).
Malware Containment and Network Protection
Provides real-time alerts to administrators about network security incidents, enabling immediate response and containment measures.
Ensures Business Continuity
Prevents malware outbreaks, data theft, productivity loss, and security policy violations.
Exclusive Features
eScan Neural Intelligence AI/ML Defense
eScan's Neural Intelligence AI/ML Defense integrates advanced machine learning algorithms with the XDR platform to enhance threat detection capabilities. The AI engine analyzes system call patterns and behavioral data to proactively identify unknown malware and evolving threats that traditional signature-based detection cannot detect. This adaptive, multi-layered approach continuously evolves with the threat landscape, providing comprehensive protection against zero-day exploits and Advanced Persistent Threats (APTs).
eScan Zero-day Defense
eScan's Zero-day Defense system employs real-time behavioral analysis and machine learning to identify and neutralize threats before conventional security measures can recognize them. Through continuous system activity monitoring and suspicious pattern correlation, the AI-powered engine detects malicious code without relying on known signatures. This proactive approach enables immediate response to emerging threats, blocking attack vectors before they can exploit unknown vulnerabilities in critical infrastructure.
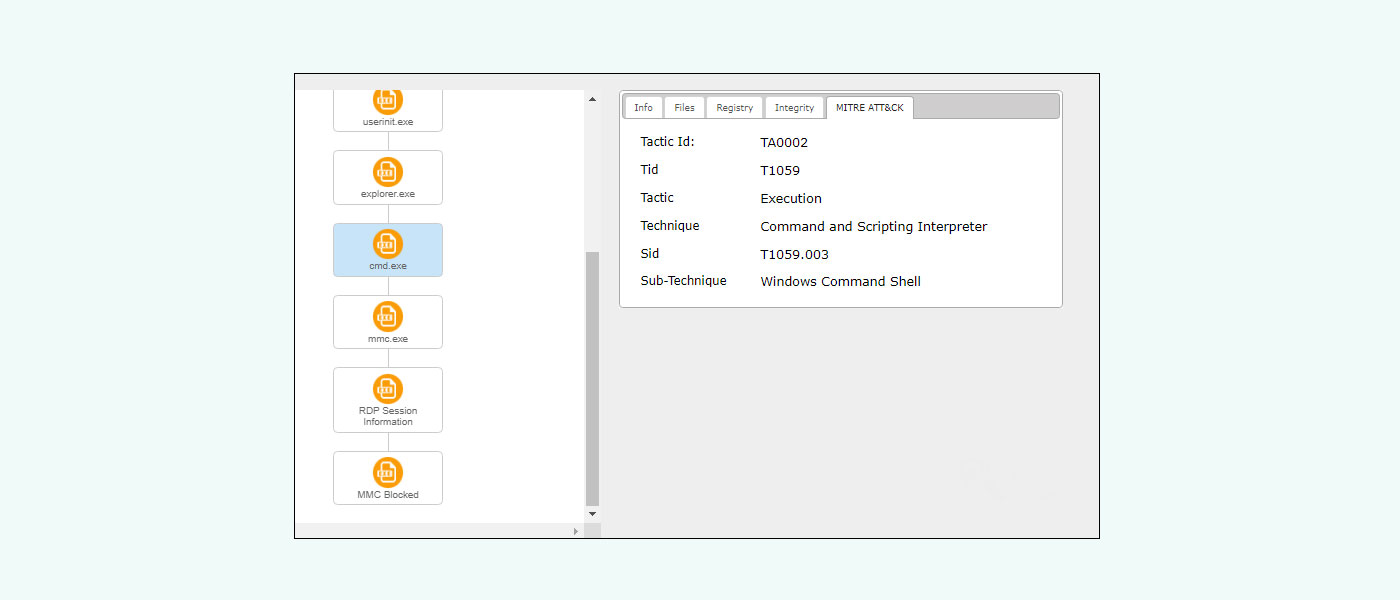
MITRE ATT&CK Framework
eScan integrates the MITRE ATT&CK framework to analyze all threat incidents detected by Vision Core XDR. The system displays detailed information about the Tactics, Techniques, and Procedures (TTPs) used in each attack. The framework provides comprehensive information about the TTPs employed by attackers during system compromise attempts. Organizational threat intelligence teams can leverage this framework to detect adversarial behavior and map observed activities to specific ATT&CK techniques, enabling better understanding of attack progression stages. This TTP intelligence facilitates threat information sharing and helps organizations stay current with evolving attack methodologies.
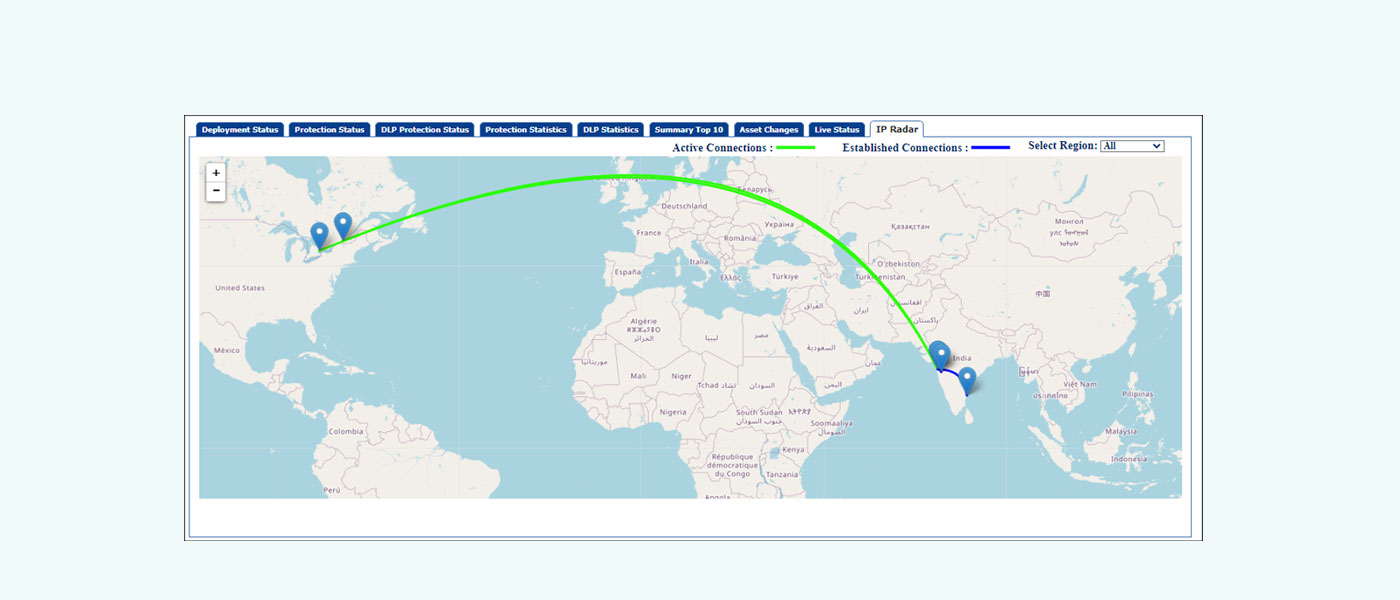
IP Radar
eScan includes IP Radar functionality in the web console dashboard, featuring a global map that displays all active and established IP connections to the eScan server. This feature enables real-time tracking of all connections currently routing through the eScan server. When IP communication occurs between XDR sensors and global resources, connections are visualized on the map using color-coded lines that indicate connection types. Administrators can filter the map view to display domestic connections, foreign connections, or all connections as needed.
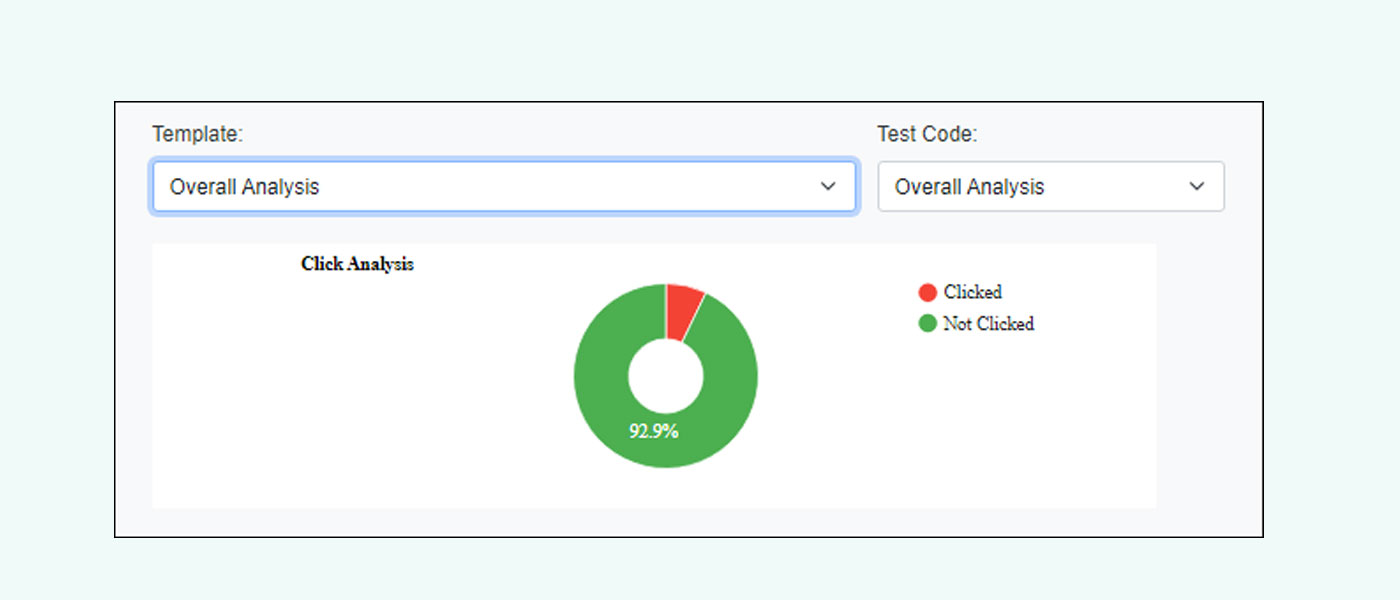
Phishing Simulation
eScan provides Phishing Simulation functionality that enables organizational threat intelligence teams to assess employee awareness of email phishing threats commonly employed by attackers. Phishing simulation involves sending mock phishing emails to employees to evaluate their response to embedded links and assess their security awareness. These simulation emails replicate the characteristics and appearance of actual phishing attacks. Employee interactions with simulation emails are logged and analyzed to identify training needs and develop targeted phishing awareness programs.
eScan Management Console - Key Features
New Secured Unified Web Interface
eScan's secure web interface employs SSL/TLS encryption to protect all administrative communications. The centralized dashboard provides administrators with graphical summaries of managed client status, including deployment status, protection status, and security statistics.
Asset Management
eScan's Asset Management module provides comprehensive hardware configuration details and complete software inventory for all managed endpoints. This capability enables administrators to maintain complete visibility of hardware and software resources across all network-connected endpoints.
Role Based Administration
Role-based administration through the eScan Management Console enables primary administrators to delegate configuration and monitoring responsibilities across multiple administrative users. This feature allows assignment of predefined roles to administrators, each with specific rights, permissions, and group access controls.
Client Live Updater
eScan's Client Live Updater captures, logs, and enables real-time monitoring of security events and endpoint status information across the entire network. Event filtering capabilities allow administrators to retrieve specific information for real-time security monitoring across all managed endpoints.
Outbreak Prevention
This feature allows administrators to implement outbreak prevention policies
that temporarily restrict network access for specific computer groups during
active security incidents.
Outbreak prevention policies apply to all selected computers and groups.
Note that improper policy configuration may cause significant operational
disruptions.
Print Activity
eScan includes a Print Activity module that monitors and logs all printing
activities across managed endpoints. The module generates detailed reports
in PDF, Excel, or HTML formats covering all print jobs from managed endpoints
to local or network-connected printers.
Note: Print Activity is available on Windows endpoints only.
One-Time Password
The One-Time Password feature allows administrators to temporarily disable
specific eScan modules on client computers for defined time periods. This
capability helps prevent users from circumventing deployed network security
policies.
Note: One-Time Password functionality is available on Windows endpoints
only.
Session Activity Report
The eScan Management Console monitors and logs session activities across all managed computers. The system generates reports covering endpoint startup, shutdown, logon, logoff, and remote session connection events. These reports enable administrators to track user logon and logoff activities, including remote session details across all managed computers.
Active Directory Synchronization
Active Directory synchronization enables administrators to align eScan
Management Console groups with Active Directory organizational units.
The system automatically synchronizes newly discovered Active Directory
computers and containers with the eScan Management Console, with configurable
administrator notifications. Administrators can enable automatic installation
and protection deployment for newly discovered Windows workstations.
Policy Templates
Policy templates simplify deployment processes by allowing administrators to create standardized policy configurations for deployment across designated managed groups.
Windows OS and App Patch/Update Management
eScan's Patch Management Module automatically updates Windows OS security patches from cloud sources or the EMC Console for computers in DMZ or air-gapped network environments. The module also reports patch availability for critical applications including Adobe, Java, and other commonly targeted software.
Endpoints Key Features
Device Control
This feature monitors USB devices connected to Windows and Mac endpoints throughout the network. For Windows endpoints, administrators can configure granular allow or block policies for USB device access. Password protection controls can block unauthorized USB device access, preventing potential data exfiltration.
Data Theft Notification
eScan sends web console notifications to administrators when writable data from client system hard drives is copied to USB devices.
Application Control
This feature enables blocking, whitelisting, and time-based restrictions for application execution on Windows endpoints. The system enforces access to whitelisted applications only, automatically blocking all unauthorized third-party applications.
Advanced Anti-Spam
eScan inspects inbound and outbound email content, providing real-time scanning for viruses, worms, trojans, and hidden malicious content using advanced heuristic-driven dual anti-virus engines. This approach prevents email-borne threats from entering the network infrastructure.
Enhanced Two-way Firewall
The bidirectional firewall with predefined rule sets restricts incoming and outgoing network traffic while preventing unauthorized access attempts. The firewall provides configuration options for IP ranges, permitted applications, trusted MAC addresses, and local IP address specifications.
Privacy Control
Privacy Control enables scheduled automatic deletion of browser cache, ActiveX components, cookies, plugins, and browsing history. The feature also provides secure file and folder deletion that prevents data recovery through third-party applications, ensuring complete data sanitization.
Advanced Web Protection
eScan includes advanced Web Protection capabilities for HTTP and HTTPS traffic, enabling administrators to configure website blocking and whitelisting policies for all managed network endpoints. Windows endpoints support additional time-based web access restriction policies.
On-Demand Scanning
eScan performs rapid endpoint scanning with minimal system resource consumption, ensuring no performance impact. This optimization ensures endpoints maintain full performance during on-demand scanning of accessed or copied files and directories. The solution offers granular scanning options for individual files, folders, directories, and running processes across managed endpoints.
Privacy Advisor
eScan includes Privacy Advisor functionality that provides comprehensive lists of applications and their device permission usage in categorized formats. This capability enables monitoring of security profiles for all installed applications.
Anti-Theft
eScan delivers comprehensive mobile device protection for Android devices, including remote data blocking, secure data wiping, SIM card monitoring, and GPS-based location tracking. The Anti-Theft feature provides complete protection against unauthorized access to Android devices in case of loss or theft.
Schedule scan
eScan performs automated scheduled scanning that operates transparently in the background without disrupting business operations. The system executes scheduled scans for selected files, folders, or complete systems according to configured schedules, providing comprehensive protection against cyber threats.

Mobile Device Scanning
Mobile Device Scanning detects viruses, malware, and suspicious files on connected Android and iOS devices when they interface with eScan-protected endpoints. This capability prevents mobile-borne infection spread and ensures connected devices meet security, cleanliness, and compliance requirements before network access.
eXtended Detection and Response (XDR) Key Features
Block executable content from email client and webmail
This rule blocks executable and script files that automatically run immediately after opening an email.
- Executable files (such as .exe, .dll, or .scr)
- Script files (such as a PowerShell .ps, Visual Basic .vbs, or JavaScript .js file)
Block all Office applications from creating child processes
Malware can compromise Office applications and manipulate them to spawn unauthorized child processes. This rule prevents all Office applications from creating child processes. The rule blocks programs from executing VBA macros, spawning commands, and using PowerShell to modify registry settings.
Block Office applications from creating executable content
Office applications can be exploited by malware as vectors for saving malicious files. These malicious files can evade detection and persist on systems to propagate infections. This rule prevents Office programs from creating and saving suspicious executable files by blocking malicious code from writing to disk.
Block Office applications from injecting code into other processes
Cybercriminals can transfer malicious code into legitimate processes through code injection techniques, making the malicious code appear legitimate. This rule prevents programs from injecting code into other running processes.
Block JavaScript or VBScript from launching downloaded executable content
Malicious JavaScript or VBScript execution can download harmful payloads or launch unauthorized background processes without user knowledge. This rule prevents JavaScript and VBScript from executing downloaded executable content.
Block execution of potentially obfuscated scripts
Cybercriminals employ script obfuscation techniques to reduce detection rates and hide malicious code within apparently legitimate scripts. This enables malware to evade detection by both human analysts and traditional cybersecurity solutions. This rule detects malicious code within obfuscated scripts and blocks execution upon identification.
Block Win32 API calls from Office macros
VBA macros in Office applications can invoke Win32 API functions. Malware exploits this capability to abuse Office applications, executing malicious shellcode directly in memory without creating disk files. This rule blocks VBA macros from invoking Win32 API functions.
Use advanced protection against ransomware
The system subjects all executable files to comprehensive authenticity verification and behavioral analysis. Files exhibiting ransomware characteristics are blocked from execution by this rule. Specific files can be exempted from this rule through inclusion in an exclusion list.
Block credential stealing from the Windows local security authority subsystem
Attackers can extract NTLM hashes and cleartext credentials from the Local Security Authority Subsystem Service (LSASS) using specialized tools. This rule prevents credential theft by blocking unauthorized access to the LSASS process.
Block process creations from WMI and PsExec commands
Windows Management Instrumentation (WMI) and PsExec enable remote code execution capabilities. Malware can exploit these features to execute malicious commands on systems and propagate throughout organizational networks. This rule prevents process creation through WMI and PsExec command execution.
Block untrusted and unsigned processes that run from removable devices
This rule blocks execution of untrusted and unsigned executable files (.exe, .dll, .scr) from removable storage devices such as USB drives and SD cards.
Block Office communication application from creating child processes
This rule prevents exploit code from leveraging Outlook vulnerabilities and protects users against social engineering attacks. The rule also safeguards against forms exploits and malicious Outlook rules that cybercriminals deploy when user credentials are compromised. While this rule prevents Outlook from creating child processes, it preserves all legitimate Outlook functionality.
Block Adobe Reader from creating child processes
Malware can compromise Adobe Reader through exploits or social engineering to download malicious payloads and maintain persistence beyond the application's normal scope. This rule blocks all child processes from Adobe Reader, reducing its potential use as an attack vector.
Block persistence through WMI event subscription
This rule prevents malware from exploiting Windows Management Instrumentation
(WMI) to establish persistent access on compromised systems.
For technical inquiries regarding eScan Vision Core XDR, contact our Enterprise
Support team at
support@escanav.com